The new IDC Survey commissioned by Fortinet offers a better understanding of the fast-changing cybersecurity landscape in APAC and the AI-driven strategies being deployed by organizations to combat emerging risks
The state of cybersecurity in Asia/Pacific is shifting from constant risk to a “platform-driven resilience,” marked by organizations embedding AI into their security strategies to combat increasingly sophisticated threats. AI-powered cyberattacks are reshaping the threat landscape across ANZ and the Asia-Pacific. An IDC Survey commissioned by cybersecurity bellwether Fortinet, encompassing 550 IT and security leaders across 11 Asia/Pacific markets: Australia, India, Indonesia, Malaysia, Singapore, South Korea, Thailand, the Philippines, Vietnam, Hong Kong, and New Zealand, sheds new light on the state of cybersecurity in the region.
In today’s era of digital business, CEOs need their CIOs to take a strategic approach to AI, which means aligning their strategy with the changing, agile demands of the business and security operations. Where cybersecurity is concerned, the reality is that security teams remain largely underfunded, under-resourced, and operate in isolation of the rest of the business. This needs to change. Threats continue to evolve, and the surge in AI-infused cyberthreats is requiring cybersecurity teams to move out of the status quo to remain effective. Complexity is the enemy of security. Organizations are using a plethora of security tools, which leads to many levels of inefficiency. Reducing and rightsizing to appropriate tools, implementing a zero trust approach, and taking the proactive approach of “assumed breach” are starting points for ongoing cybersecurity success. With cybersecurity teams rushing at full tilt to simply stay secure, reducing the number of tools to a more manageable platform and embedding it with the necessary AI and automation tools is now critical.

“Trusted AI is critical to ensure AI-driven systems are both effective and trustworthy, and the cybersecurity control points are at the heart of trusted AI.”
– Simon Piff, Research Vice President, IDC Asia/Pacific
Efficiency and Risk Management Top Priorities, Raising the Stakes for AI
With operational efficiencies and risk management at the forefront of the CEO’s agenda, AI stands out as a leading technology aligned with these strategic goals. Underpinning the success and value of AI is security, as organizations integrate various forms of AI, including machine learning and GenAI, to drive efficiency into cybersecurity operations and address other priorities such as environmental, sustainability, and governance (ESG) reporting compliance. CIOs and security teams have their work cut out for them, as they seek ways to address concerns around the security and sanctity of the raw data that powers AI.
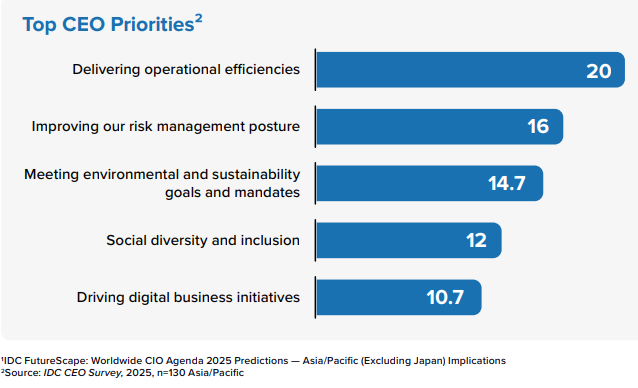
IDC predicts that in 2026, 50% of CIOs will diversify and broaden security strategies across their organization’s IT and security teams to address new or fast-evolving threats to their technology and supply chain ecosystem.1 CIOs who effectively leverage AI to protect their IT infrastructure can improve organizational resilience, positioning their organizations as leaders in cybersecurity effectiveness.
AI Conundrum Not a Deterrent for Forward-Looking Businesses
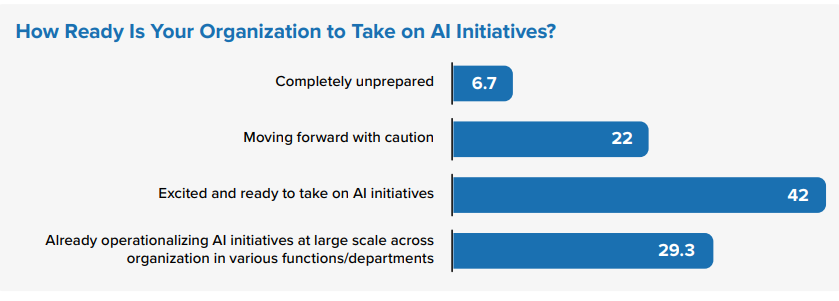
Cybersecurity remains a significant challenge for many organizations today, compounding concerns around whether their data, edge environments, and infrastructure are ready and secure for AI deployment. But even as AI adds further complexity and demands enhanced security, inaction poses the bigger risk of losing business competitiveness. About 30% of CEOs surveyed said their organizations are already delivering operational AI — putting themselves ahead of the pack — while 22% are still too cautious to move ahead.
AI Intensifies Need for Cybersecurity, But Funding Remains a Fraction
AI is transforming both sides of the cybersecurity equation, equipping security teams with new capabilities to strengthen defenses while also enabling threat actors to enhance their success rates. Almost 61% of organizations across Asia/Pacific say they have encountered AI-powered cyberthreats in the past year. Of those, 64.2% reported a 2x increase and 28.9% reported a 3x increase in threat volume. These attacks are harder to detect and often exploit blind spots in visibility, governance, and internal processes. Despite Threats, Budgets Continue to Be Modest While 30% surveyed are already operationalizing AI initiatives at large scale across their organizations, slightly less than 10% of revenue is spent on IT, and less than 1.5% on cybersecurity.
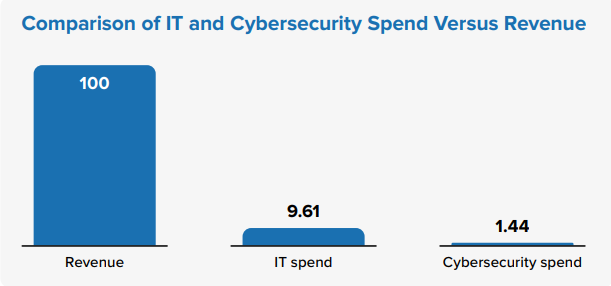
Clearly this data would change based on industry, attitude to technology, and ability to leverage technology investments, but this data should serve as a benchmark for what is considered “average”. IDC notes that some markets spend significantly less on both technology and cybersecurity, which needs to be examined, since the threats are growing.
Businesses Under Siege as AI-Driven Cyberattacks Surge
AI-powered threats are scaling fast with devastating effect. Harder to detect, they appear as legitimate users, either through password attacks or deepfakes. This type of attack is set to rise, creating a whole new set of threats that will require incredibly agile security teams. Add these identity hijackings to the impact of human-based threats, and cybersecurity teams have to step up their overall capabilities with significantly higher levels of efficiency.
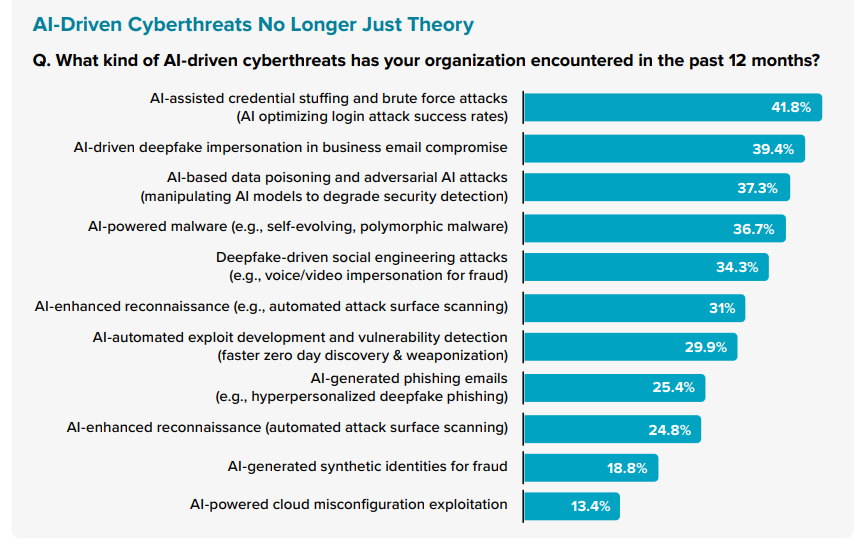
The top 5 AI-driven threats encountered across the Asia/Pacific region include credential-based attacks, impersonation and business email compromise (BEC) scams, data poisoning and adversarial AI, self-evolving malware, and intelligent scanning of attack surfaces. These AI-driven attacks can only be achieved with the help of more effective tools, enhanced with AI and automation to boost the effectiveness of cybersecurity teams.
The Growing Onslaught: Persistent Cyberattacks Across All Fronts
The nature and growth of threats have evolved in recent years, with today’s cybersecurity landscape in a state of constant exposure. Software supply chain attacks, which exploded into view in 2021, are not only the most significant threat but also the fastest growing. Ransomware is also one of the most well-recognized cyberthreats among C-suite executives due to its frequency and potential as a damaging threat to the business, though just a notch lower than software supply chain threats which are prioritized among security professionals too. Regardless of the type of threat, they are all increasing in frequency, and this is not expected to change. Unless internal skills and toolsets are updated to address this onslaught, organizations increase their vulnerability to fast-evolving threats, in which different threats carry different payloads of damage.
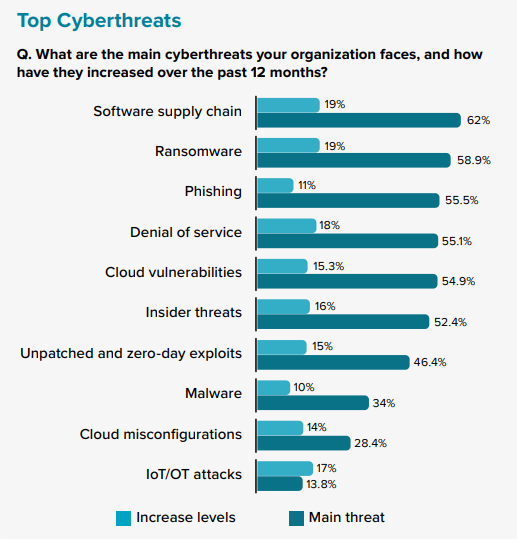
Not All Threats Are Equal: Going Beyond Patching to Breach Discovery
Staying patch-current has long been a challenge for many organizations across the region. The acceleration and impact of unpatched and zero-day exploits is seen to be the most challenging for organizations across the Asia/Pacific region. Given the challenges in patching, tools that identify and contain such threats need to be strengthened until patches can be applied. Human-based threats deliver significant impact, with insider threats causing substantial damage due to their hyperpersonal nature. Threat actors intimately know what will have the most impact. Cloud misconfiguration is rife, exposing data and often personally identifiable information (PII), resulting in fines and brand or reputational damage Human error, an almost unavoidable threat, also appears high in the impact scorecard. Since these threats are almost unavoidable, the onus needs to shift to higher levels of monitoring to minimize time to identify and neutralize any such threat. This is where the approach of “assumed breach” plays particularly well. In the event of a breach, the focus shifts to discovery.
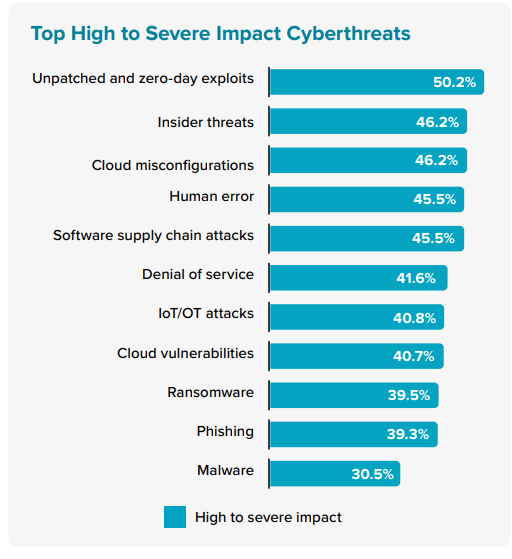
Beyond Data Loss: Damage to Reputation and Customer Trust
While data is the key asset generally being stolen, the impact is often widespread and leads to multiple issues. Reputational damage and loss of customer trust can have significant, long-lasting effects on a business, making it difficult for the company to rebuild its image. The impact of punitive fines and non-compliance can magnify brand issues and lead to loss of revenue. In today’s context of digital business, operational downtime equates to loss of revenue, forcing security to be viewed as a business risk and not just an IT issue. The assumed breach mindset of cybersecurity teams shifts the focus from solely preventing breaches to proactively detecting, identifying, responding, and remediating vulnerabilities. This is critical for digital resilience. The next question is: How quickly can businesses recover from the inevitable?
Security Teams Under Pressure Amid Shortage
The average security team is lean and often lacks significant leadership alignment. Only 15.6% of organizations have a standalone chief information security officer (CISO), and 63% continue to combine cybersecurity responsibilities with broader IT roles. Just 6.4% of organizations have specialized teams for functions like threat hunting and security operations. This lack of specialization is impacting performance. More than half of the respondents cited an overwhelming surge in threats, with additional pressures from tool sprawl and talent retention challenges. Execution suffers as teams struggle with burnout and complexity, reinforcing the need for more intelligent resourcing models. Embedding AI and automation within the toolsets is one way to address resource constraints. Shifting to security platforms, rather than individual feature-rich applications, will also help drive efficiencies into the operations of cybersecurity when internal skills are lacking.
Strategic Investments: From Infrastructure to Intelligence
Cybersecurity budgets are on the rise, with nearly 80% of organizations reporting increases. Yet spending remains cautious, with most increases under 10%. Organizations are shifting from infrastructure-heavy spending to more strategic priorities.

The top 5 investment areas for the next 12–18 months are identity security (50.5%), network security (45.3%), cyber-resilience (45.1%), SASE/zero trust (45.1%), and cloud-native application protection (43.1%). These priorities suggest a more structured, risk-centric investment strategy aimed at addressing modern, distributed threats. However, operational and human-layer areas such as OT/IoT security, DevSecOps, and training continue to be underfunded, reflecting ongoing blind spots.
AI Skills Redefining Cybersecurity Roles
The top 5 cybersecurity roles in demand include security data scientists, threat intelligence analysts, AI security engineers, AI security researchers, and AI-specific incident response professionals. Organizations are no longer just deploying AI tools — they are building their cybersecurity teams around AI capabilities. This reflects a broader trend where the workforce is rapidly evolving to match the pace of technological adoption.
AI Adoption in Security Moving from Pilot to Production
AI is becoming an integral part of security operations. More than nine in 10 organizations across Asia/Pacific are already using AI in their security environments. About 53.8% are developing in-house AI applications and 38.4% are relying on vendor-embedded capabilities. Organizations are rapidly progressing from AI-powered detection to more advanced use cases such as automated response, predictive threat modeling, AI-driven incident response, AI-powered threat intelligence, and behavioral analytics. These top 5 use cases reflect how detection has become table stakes — while response, prediction, and orchestration represent the next frontier of the cybersecurity landscape. GenAI is also gaining traction, with adoption focused on light-touch tasks. The top GenAI-driven cybersecurity capabilities are updating rules and policies (32%), running playbooks (32%), social engineering detection (30.9%), writing detection rules (30.5%), and guided investigations (30.2%). Trust in autonomous action remains limited. Use cases like auto-remediation (10.4%) and guided remediation (2.4%) are a rarity. Trust in AI outputs is still being monitored closely, and whilst we move to the era of agentic (AI telling AI what to do) it will be a while before homegrown AI can be fully operational. Whilst vendor AI is likely to be more robust, internal AI projects are only as secure as the quality of data inputs, which in Asia tends to be challenging.
A Holistic Strategy Starts with Zero Trust
Zero trust has become the only way to address the assumed breach approach. Principals of zero trust are becoming more well understood, although implementations due to tool sprawl are driving a degree of complexity that is slowing down its rollout.
Securing AI Requires Cross-Functional Teams Built on Trust
Trusted AI is critical to ensure AI-driven systems are both effective and trustworthy, and the cybersecurity control points are at the heart of trusted AI. With AI spanning the organization, it breaks down data silos and forces lines of business as well as IT to work as a single unit. It is imperative that the security team is part of the organization’s AI center of excellence if secure and trusted AI is to be successfully delivered. To achieve this, cybersecurity teams need to be able to deliver more effective outcomes.
Consolidation and Convergence Become Core Strategies
As complexity grows, organizations are prioritizing platformization to unify operations, improve visibility, and reduce costs. Nearly all respondents (97.1%) are either converging security and networking or evaluating how to do so. While many organizations now use just one to five security tools, tool fatigue remains widespread due to poor integration.
Consolidation is no longer viewed as just a cost-cutting measure — it’s seen as a strategic necessity. About 79% of respondents are actively considering vendor consolidation, driven by benefits like faster support (58.9%), cost savings (53%), better integration (52.8%), and improved security posture (51.4%). That said, roadblocks persist. About 61% cite budget constraints as the top challenge, followed by concerns around vendor lock-in (43.9%) and interoperability (43%). Cultural resistance also plays a role, with 38.6% pointing to internal opposition to change. IDC surveyed 550 IT and security leaders across 11 Asia/Pacific markets. Respondents represented organizations with over 250 employees and were directly involved in cybersecurity decision-making. The survey was conducted between February and April 2025.