By Manash Ranjan Debata
What’s embarrassing for CrowdStrike is that despite its big claims of higher security credentials, the errant update has soiled its name. The fact that its errant and irresponsible update has crippled businesses around the world can’t be denied.
On July 18, 2024, in an awful and unfortunate incident an update from the cybersecurity company CrowdStrike badly impacted IT systems globally, leading to widespread disruptions. The security breach, although it’s claimed wasn’t caused directly by CrowdStrike, what’s evidently clear is that the issue stemmed from a faulty update to CrowdStrike’s antivirus software, which is designed to protect Microsoft Windows devices from malicious attacks.
Whatever way the naysayers may try to play down the incident, what’s embarrassing for CrowdStrike is that despite its big claims of higher security credentials, the errant update has soiled its name. The fact that its errant and irresponsible update has crippled businesses around the world can’t be denied. The errant update affected approximately 8.5 million Windows devices worldwide, causing huge loss and inconvenience to businesses and users.
Microsoft has been firefighting with all its might. It’s working closely with CrowdStrike to understand the nature of the breach to find a way out of the impasse and provide technical guidance to affected customers.
Thankfully, both companies have claimed that the incident has been resolved, and they are actively collaborating to prevent such occurrences in the future. But the fact of the matter is it has already done much damage before being reigned in.
Big Admission by CrowdStrike
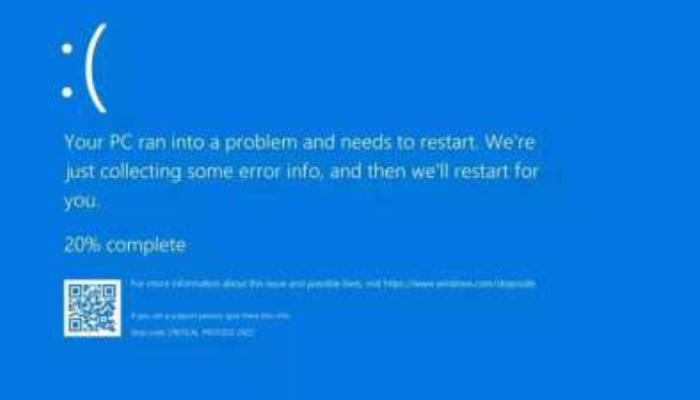
Security experts have dubbed the CrowdStrike outage as the “largest IT outage in history” and “easily the worst… glitch of any security software provider ever.” CrowdStrike, too, has admitted that a “defect” in a software update that it sent out to its customers on July 18 caused millions of computers using Microsoft Windows to crash. Users reported that their computers have been constantly rebooting and displaying the so-called “blue screen of death.”
Affected Parties Mulling Legal Action
Already businesses that are affected by the outage have been actively looking for legal remedies against the entities responsible for the incident. Gibbs Law Group is investigating a potential class action lawsuit on behalf of business owners whose operations were disrupted due to CrowdStrike’s defective software. This includes businesses that aren’t even CrowdStrike customers but suffered due to essential payment and data systems crashing.
Embracing “Blue Screen of Death”
So, who caused this? Whom to hold responsible for the unfortunate incident? Well, it’s crystal clear that the recent global tech outage was caused by a faulty update from CrowdStrike. The routine software update from CrowdStrike, a cybersecurity company widely used by businesses and government agencies running Microsoft Windows, triggered a massive global IT outage.
The issue affected various sectors, including airports, banks, retail, and law enforcement systems. CrowdStrike’s “Falcon Sensor” software caused Windows computers to crash, displaying the infamous “Blue Screen of Death” (BSOD).
The flaw originated from a single content update that impacted Windows hosts, specifically a kernel-level driver used for securing Windows machines.
Mac and Linux: Outside the Purview
While Windows systems continued to bleed, what’s interesting is that Mac and Linux systems remained unaffected and unimpacted by the breach. This again brings into sharp focus the indefatigability of the Mac and Linux. The fact that they are highly impenetrable compared to Windows-based systems is all the more pronounced from this incident. This also underlines the vulnerability of Windows-based systems.
The Firefighting
So, how did they manage to bring the incident under control. CrowdStrike promptly deployed a fix to address the issue. Microsoft and CrowdStrike collaborated to rectify the situation and to prevent and guard against such occurrences in the future.
Although the disruptions weren’t a deliberate breach, the incident underlines the criticality of rigorous testing and quality control in software updates.
Global Business Disruptions
CrowdStrike software update glitch has already caused significant repercussions for businesses and individual users globally. Banks in the Philippines, including BPI, BDO, and RCBC, were severely affected. Airlines, hospitals, and public transit systems faced disruptions due to the faulty update. Similarly, emergency call centers experienced downtime, impacting critical services.
Global Scale
The incident affected approximately 8.5 million Microsoft Windows devices worldwide. Thousands of flights were delayed or canceled.
Market Share Impact
Given that CrowdStrike is used by over half of Fortune 500 companies, it can be safely emphasized that it has widespread adoption. And because of this, the impact of the breach was widespread. Microsoft’s Windows OS dominates globally, with an estimated 85% usage in federal government productivity software.
Robust Regulatory Guardrails: Need of the Hour
As economies are getting increasingly digitized, their reliance on global technology platforms is all set for continuous expansion. This means such events will not only be more prevalent but also more painful in coming days. This calls for stricter regulatory practices on the part of the governments, when it comes to data protection and to guard against tech outages like this.
Thus, the incident underscores the need for robust regulatory guardrails to prevent similar outages in the future.
In short, the CrowdStrike glitch that disrupted businesses, services, and critical infrastructure, further highlights the interconnectedness of our digital world and the need for care and caution while running such software testing or updates.
How Businesses Can Mitigate Such Issues
So, what steps can businesses take to mitigate such incidents in the future? Well, in order to mitigate incidents like the CrowdStrike software update glitch, businesses can take several proactive steps:
They should update and upgrade their software at regular intervals. They should apply all software updates promptly and automate the process if possible. Similarly, they should make it a point to use updates delivered through protected links and test them before production release.
Care should be taken to limit and control account access. They should implement a zero-trust framework and assign account privileges sparingly. They should securely reset credentials and consider using privileged access management tools.
They should also ensure that their operating system uses secure boot and enforces signed execution policies for scripts, executables, drivers, and firmware. Similarly, they should avoid allowing unsigned software to prevent cybercriminal entry points. Businesses should formalize a Disaster Recovery Plan (DRP); Craft a dynamic DRP covering business continuity, data protection, restoration, backups, system reconstitution, and logs; and continuously review and update the DRP as part of their risk management plan; and actively Manage Systems and Configurations.
In short, proactive planning and continuous improvement are essential for effective cybersecurity risk management. Similarly, effective incident response planning is crucial for minimizing the impact of security incidents.
Do let us know your views at manash@accentinfomedia.com