The latest threat insight from Barracuda has revealed that between June and September 2022, the top threats were successful Microsoft 365 logins from a suspicious country, accounting for 40% of attacks from suspicious countries. Followed by communication from the network to a known dangerous IP address (15% of attacks), and brute force user authentication attempts (10%).
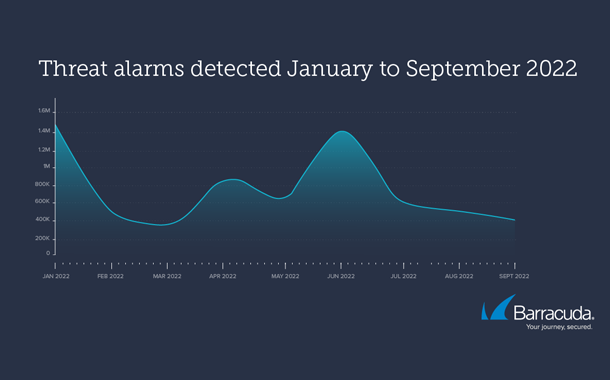
The research shows the severity of the attacks has witnessed a huge spike as 1 out of 5 (96,428) attacks were highly critical and reported between June to September 2022 as compared to 1 out of 80 (17,500) in January 2022. Experts at Barracuda analysed 4,76,994 threat alarms from June to September out of which 20% amounted to 96,428 were alerted and urged to take remedial actions.
Amongst the top detected threats, successful Microsoft 365 login from a suspicious country is classed as ‘high risk’, which have the potential to cause severe damage and demand immediate action. This attack accounted for 40% of all attacks during the 90-day window. The countries that flag an automatic security alert include Russia, China, Iran, and Nigeria. A successful breach of a Microsoft 365 account offers an intruder potential access to all the connected and integrated assets the target has stored on the platform. Among other things, analysts look for evidence of multiple-country logins to the same account.
Communication to an IP address to Threat Intelligence and brute force authentication user attempt are classed as ‘medium risk’, which requires mitigation but would not typically lead to substantial impact as a standalone event. The attacks accounted for 15% and 10% respectively, where the former includes any attempt at malicious communication from a device within the network to a website or known command-and-control server etc., and the brute force authentication user attempts are automated attacks trying to penetrate an organization’s defences by simply running as many name/password combinations as they can.
“Cyber attackers target companies and IT security teams during off hours like weekends, overnight, or during a holiday season, such as the summers and festivals”, said Parag Khurana, Country Manager, Barracuda Networks India.
“Businesses should reinforce essential security measures such as enabling multifactor authentication (MFA) across all applications and systems, ensuring all critical systems are backed up, implementing a robust security solution that includes email protection, web application firewall (WAF) and Endpoint Detection and Response (EDR) in order to monitor, detect, and respond to cyberthreats,” he added.